Cyber threats are constantly adapting and evolving, making it increasingly difficult for companies to protect their networks and data. To stay ahead of these threats, it is necessary to have a comprehensive cybersecurity strategy that employs multiple layers of security.
This approach can help mitigate the damage caused by cyber attacks and can also help to prevent them from happening in the first place. Nearly 7 million phishing and other malware sites were created just in 2020. The growth of these cybersecurity risks will continue to increase, so it’s vital to take action now against these threats.
In this post, we’ll discuss elements of cybersecurity strategy that can keep your business protected from cyber criminals.
What is a Layered Security Approach?
A layered security approach is a cybersecurity strategy that employs multiple layers of protection. This method can provide additional support to areas in the system or types of information that are the most vulnerable.
The layers that make up a layered security process can include any of the following:
- Firewalls – These act as a barrier between your network and the outside world, preventing unauthorized access and protecting your data. Firewalls work by inspecting all traffic that passes through them, and they can block or allow traffic based on predetermined rules.
- Operating System Updates – Operating system updates can reinforce your cybersecurity posture by patching vulnerabilities that can be exploited by cyber criminals. By keeping your operating system up to date, you can reduce the chances of being hacked.
- Security Awareness Training – Educating employees about the dangers of cybercrime and how to identify phishing emails can reduce the risk of a successful attack. Security awareness training can help employees understand how to protect themselves online by teaching them how to spot malicious emails and websites.
- Password Protection – This security measure can help protect your computer or network from unauthorized access. Password protection works by requiring users to enter a password before they can access the system. These passwords should use numbers and special characters to increase their strength and be changed frequently for increased protection.
- Multi-Factor Authentication – Multi-factor authentication (MFA) is a security process that requires more than one form of identification to access a system or account. This can include something the user knows (a password), something the user has access to (a security token), or something the user has (a fingerprint).
Making use of these tools for your business’s layered security will benefit your company by preventing the possibility of a successful cyber attack. Apply these layers to your cybersecurity strategy for optimal protection.
Top Growing Cyber Threats to Look Out For
There are cyber risks that continue to improve in sophistication to avoid being detected. Malicious attacks were shown to be the cause for 51% of data breaches in 2019. It’s essential to recognize these changes to attack tactics and know some of the most common cyber threats to look for. Here are a few of them:
1. Social Media Scams – Scammers are increasingly using social media platforms to target users with fake deals, offers, and contests. These scams can be difficult to spot, as they often look legitimate. Be aware of these scams and never click on links or provide personal information in response to a message from someone you don’t know.
2. Ransomware – This type of malware encrypts a user’s files and demands a ransom be paid to decrypt them. Ransomware can be devastating for businesses, as it can result in the loss of important data. To protect against ransomware, create a backup of your data in a secure location.
3. Phishing – Phishing attacks trick users into providing personal information or clicking on malicious links. Phishing emails often appear to be from a legitimate company or online retailer. Never click on links in emails from senders you don’t know, and be careful when providing personal information online.
4. Malware – Malware is a type of software that is designed to damage or disable computers. Malware can be used to steal personal information, destroy data, or take over a computer. There is software available to protect your computer from malware attacks; make sure to keep it updated.
5. SQL Injection Attacks – These attacks take advantage of vulnerabilities in web applications to inject malicious code into a database. This can allow attackers to access sensitive information. To protect against SQL injection attacks, keep your software updated.
By recognizing the signs and content associated with these cybersecurity threats, you’ll be better able to protect your company by strengthening and following your cybersecurity strategy.
Benefits of Layered Security Approach in Fighting Cyber Threats
A layered security approach provides multiple lines of defense against cyber attacks, making it more difficult for hackers to penetrate your system. This approach uses a variety of security measures that work together to protect your data.
By using a layered security approach, you can make it more difficult for hackers to access your system and reduce the chances of a successful attack. Contact RESULTS Technology now for a security risk assessment to strengthen your system’s security.

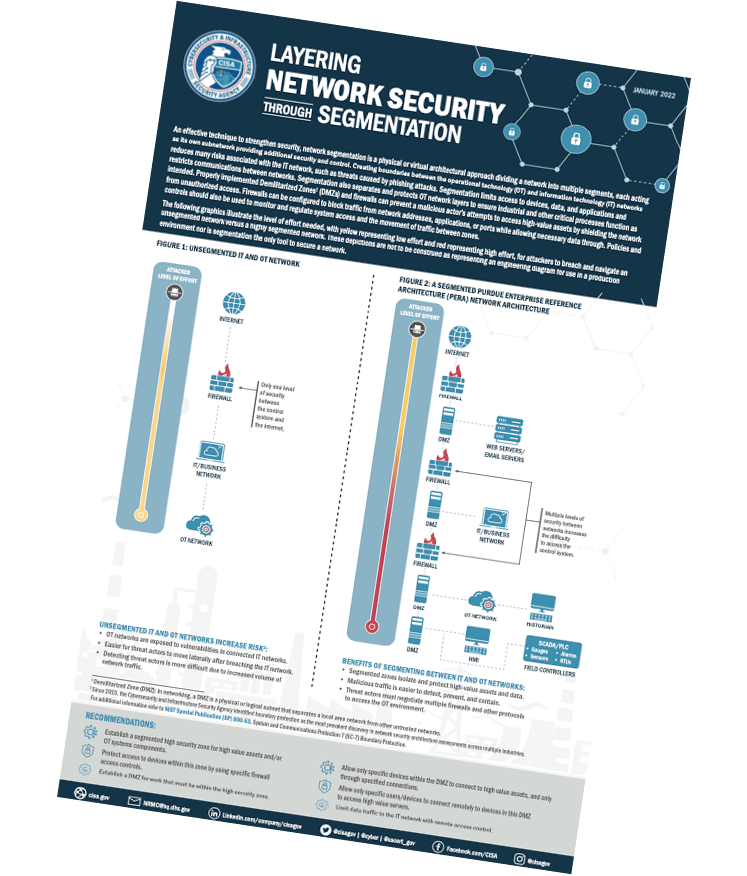
LAYERING NETWORK SECURITY THROUGH SEGMENTATION
Free Download